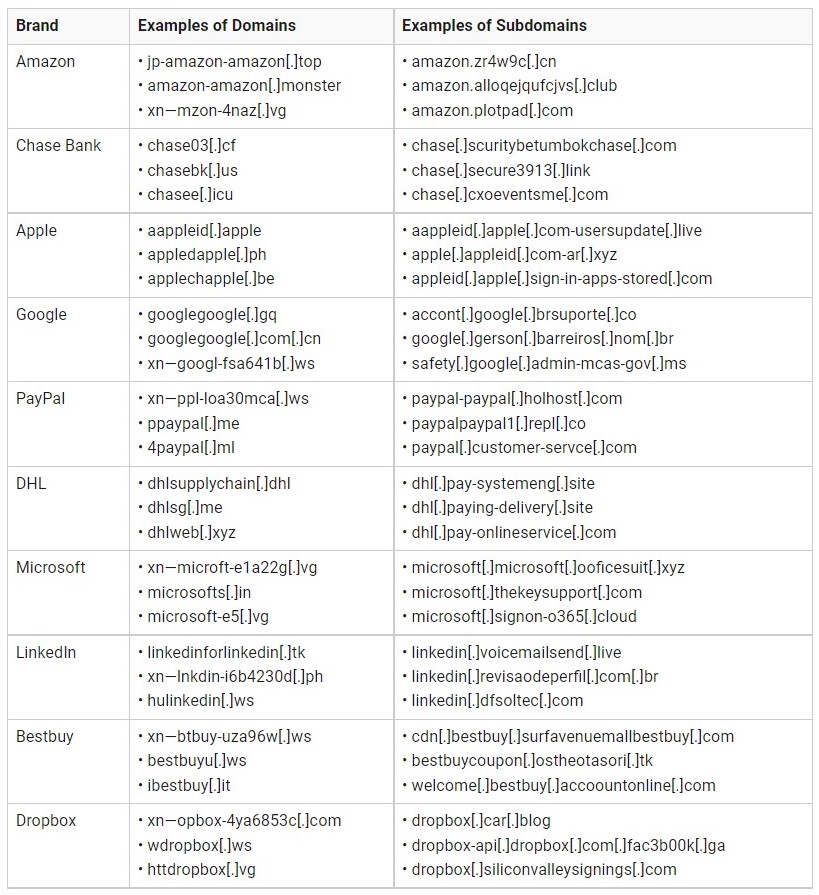
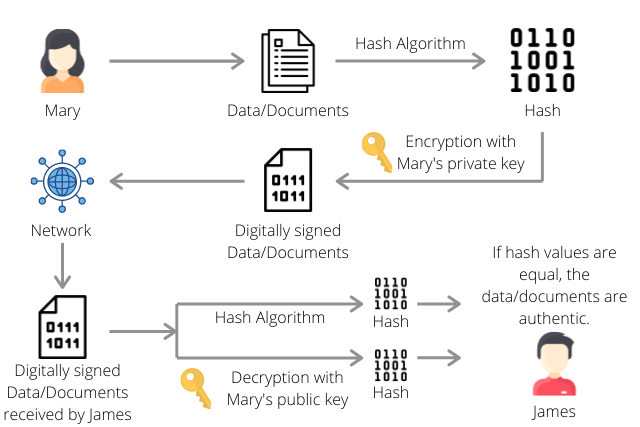
A root certificate used by Let’s Encrypt has expired and caused problems for some companies and users.

The specific root certificate mentioned here that expired on 30 September 2021 is the IdenTrust DST Root CA X3. It was created back then in the year 2000, which has a validity period from 30 September 2000 to 30 September 2021. Most people probably won’t be affected by this expiry problem, but certain groups of people or companies have definitely come across some problems caused by this expiry, particularly those that that are still using old devices, old system infrastructure or old versions of operating system.
To understand the reason why this happens, it is important to know about how Certificate Authorities (CA) work and how the SSL certificate chains work. It is important to understand the concept of chain of trust in terms of SSL certificate, which is the foundation of the entire SSL certificate industry.
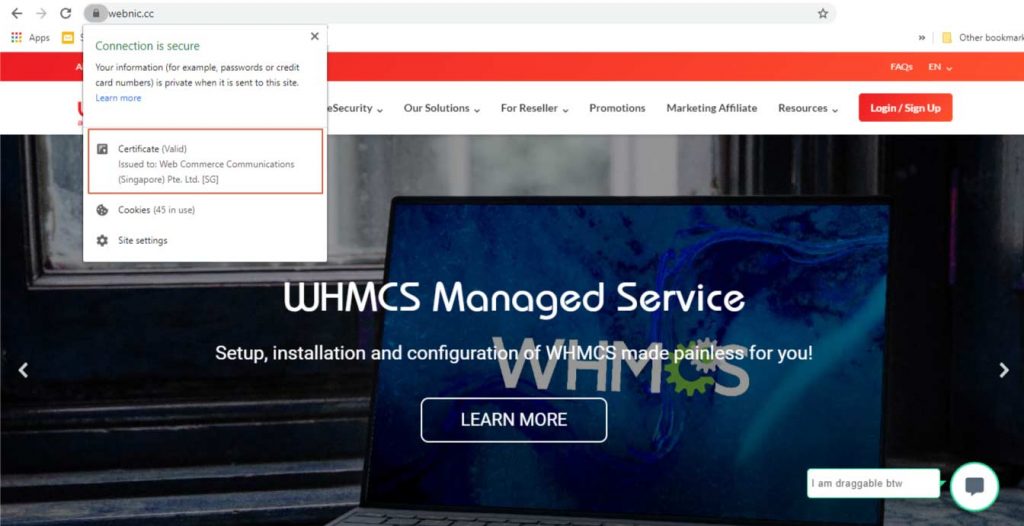
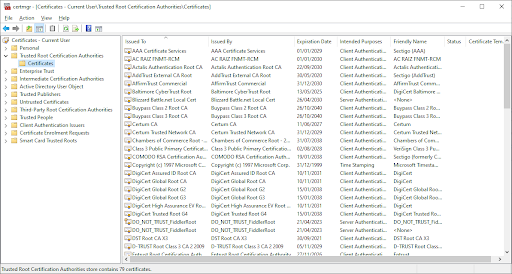
To make it simple, all certificates that enable HTTPS on the Internet are issued by a CA, an organisation that is trusted and accepted by devices or operating system (OS). For example, the image below shows the list of “Trusted Root Certificate Authorities (CA)” on a Windows 10 device.
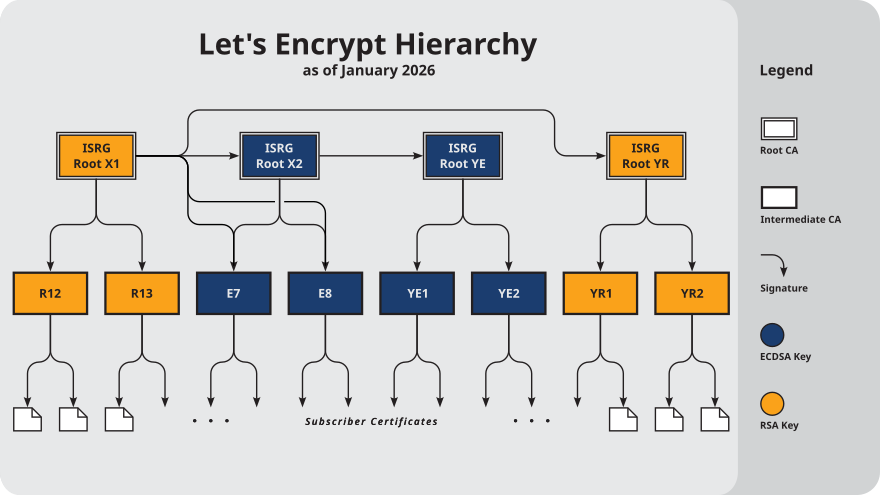
The different levels in the hierarchy of SSL certificates
SSL certificate is usually categorised into 3 levels of hierarchy, the top-level root certificates, followed by the second level intermediate certificates and lastly the third level leaf certificates or end-entity certificates.
CA function as an entity to issue root certificates, which is the top-most level in the hierarchy of the certificate chain of trust. Most of the time, they are typically valid for around 20 years. These root certificates are then used to issue the second level intermediate certificates, which are typically valid for around 3 – 6 years. The intermediate certificates are then used to issue the third level leaf certificates, the ones that websites around the world get. They are typically valid for around 90 days to 1 year.
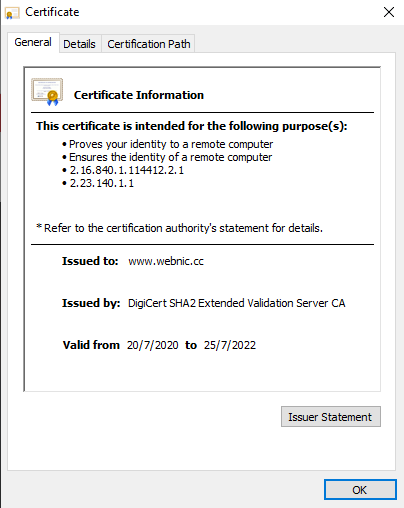
These 3 levels of SSL certificate work together to establish a chain of trust, which serves as the foundation of how the SSL certificate industry works. Leaf certificates are chained to intermediate certificates, while intermediate certificates are chained to root certificates. In the case of the expiry of Let’s Encrypt’s root certificate, IdenTrust DST Root CA X3, the image below shows its chain of trust.
Let’s Encrypt root certificate expiry

Now that IdenTrust DST Root CA X3 has expired, any users of SSL certificates that were chained to this root certificate will face problems when trying to access the Internet. Some services by famous brands might also face interruptions in delivering their service to end users due to this problem. As the scale of usage of Let’s Encrypt’s SSL certificate is very large, probably millions of people or companies will be affected, particularly those that use old devices, old system infrastructure or old versions of operating system as mentioned above.
Scott Helme, a security researcher, entrepreneur and international speaker who specialises in web technologies, listed in his blog the clients that will break after the IdenTrust DST Root CA X3 expires. These include versions of macOS older than 10.12.1, Windows versions older than XP Service Pack 3, iOS versions older than iOS 10, OpenSSL versions less than and including 1.0.2, and Firefox versions older than 50.
What happens when a root certificate expires?
Let’s Encrypt’s Executive Director, Josh Aas, mentioned that when leaf certificates (end-entity certificates) expire, it typically has very little impact, as it only pertains to a small number of websites and they renew automatically. However, when root certificates expire, there can be more widespread impact because the number of certificates chained to them is larger, hence client operating systems or browsers may need to be upgraded to fix problems. However, that isn’t always an option for older devices or deployments.
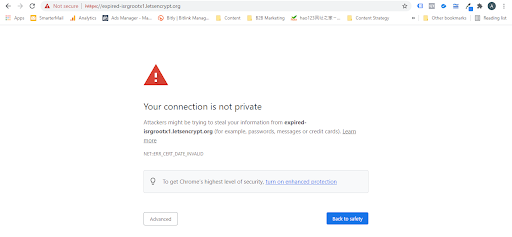
When root certificates expire, most clients’ devices or operating systems will automatically update the system list of “Trusted Root Certificate Authorities (CA)”, and the expired root certificate will be automatically removed through system updates. From here onwards, whenever the clients come across any SSL certificate that chains from the expired root certificate, an error occurs. An example of the error message of an expired SSL certificate is shown below.
A note worth mentioning is that the browser Firefox maintains its own list of trusted root certificates, independent from a system’s built-in list. You can learn more about it here.
Conclusion
As Let’s Encrypt SSL certificate comes free, therefore the team behind it is not really required to provide users with any service commitment in situations like this. When it comes to issues like this, it is up to the user’s technical capabilities to solve them. The best there is to offer is the community forum support from the people who are passionate about it.
Besides, with the recent outages of mainstream services such as Facebook, Instagram and WhatsApp, which went down for 6 hours on October 5, 2021, it is important to advise your customers to have a backup plan for their online business, in case unfortunate events all happen at the same time and affected their business operations severely.

The best advice you can give to your customers is to always build their own website, instead of relying on free services, as mainstream service is not a guarantee that it will last until the end. With this in mind, WebNIC wants to help you to assist your customers in building their website and owning their domain names. You can now pay a very little amount to get a DV SSL certificate (from as low as USD4.00 only) for 1 year, with access to guaranteed support from WebNIC. Let your customers know that having a website is much safer, because if social media dies off, at least they would not disappear completely with it in the online world, because there is still a backup ready.
Register domain and buy SSL certificates for your customers with WebNIC

WebNIC is an accredited registrar of over 800 TLDs and a trusted provider of more than 50 brands of SSL certificates to suit your different needs. We have more than 20 years of experience in the domain wholesale and reseller service, as well as more than 7 years of SSL certificate experience. You can be assured that we will provide the best service experience in helping you to register domains and buying SSL certificates. Join WebNIC as a domain and SSL certificate reseller to start selling with us today!
About WebNIC

WebNIC operates a digital reseller platform covering primarily domain name registration for over 800 TLDs, web security services, email and cloud services. With offices in Singapore, Kuala Lumpur, Beijing, Taipei and Jakarta, we serve 5,000 active resellers in over 70 countries. With over 20 years’ experience, we accelerate our partner’s growth through a robust platform, attentive support and wholesale pricing. To join us and become a reseller, live chat with us or email us at [email protected].